We all know not to share our passwords publically. Most people are smart enough not to share other identifying details publicly, like their home address, date of birth, or a photo of their credit card, yet people keep doing all these and more, opening us to theft, identity theft, harassment, and for the criminally-inclined, getting caught and a conviction. Here are some mistakes people make, sometimes commonly, without realising the implications.
Contents
Posting A High-Resolution Photo Of Your Hand, and Unwittingly, Fingerprints

Drug dealer Carl Stewart, 39, from Liverpool, learned this the hard way when he posted a photo of some cheese in a local supermarket. . Police had infiltrated the encrypted criminal messaging service EncroChat where the photo was posted, and were able to identify the individual because the photo was high enough resolution to show his fingerprints.
Has anyone been framed based on recreated fingerprints? Not yet, but perhaps it’s a matter of time.
Posting A Photo of Your Mailing Address, Even With The Address Blacked Out
When Australian YouTuber (I guess we’re now calling them “influencers”?) communitychannel aka Natalie Tran posted the following tweet to her quarter-million followers, I knew right away she’d just shared her address with the world, even though she blacked out the address. Can you tell how?
https://twitter.com/natalietran/status/892232436058210304?ref_src=twsrc%5Etfw%7Ctwcamp%5Etweetembed%7Ctwterm%5E892232436058210304%7Ctwgr%5E%7Ctwcon%5Es1_&ref_url=https%3A%2F%2Fwww.smh.com.au%2Fbusiness%2Fconsumer-affairs%2Fhow-is-this-legal-insurer-aami-criticised-for-ad-that-looks-like-bill-20170801-gxn10p.html
The Intelligent Mail barcode (IM barcode) at the top can be reproduced to send mail to her. It can also be entered into a reverse lookup site or software to get the mailer ID or even address if you’re crafty enough. Or just recreate the barcode, and put a GPS tracking keyring in the post and see where it goes.
In Natalie’s case, the story made The Sydney Morning Herald, a mainstream news publication, getting even more exposure, proving that journalists are ignorant of the fact that they may as well be sharing someone’s address. It’s surprisingly common.
Take this low-resolution photo posted on The Daily Californian which is too low resolution to make out an address, but clear enough to read the barcode.

Posting Your Boarding Pass
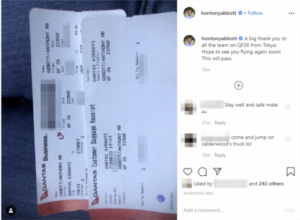
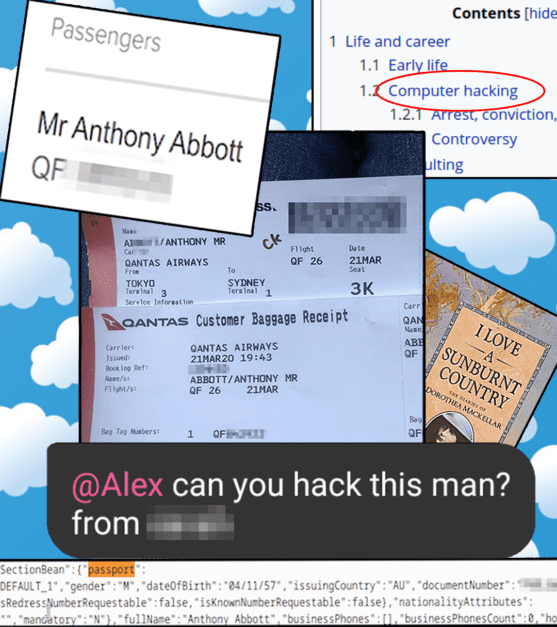
When former Australian Prime Minister Tony Abbott posted his boarding pass to his Instagram, hacker Alex Hope (aka mangopdf) took the challenge to see what he could do with it. At the time he was able to determine passenger:
- passport details
- phone number
- comments between airline staff
Other data a skilled person can gain access to include
- email address
- date of birth
- frequent flyer number
Amir Tarighat, CEO of cybersecurity firm Agency told USA Today that “Frequent flyer miles are actually really easy to steal, and they kind of don’t have the same protection that banks have,” adding that travel accounts are commonly sold on the Dark Web.
Alex Hope tried his best to alert both the airline and former Prime Minister’s office of the holes in the system that exposed this information, which were fixed by the time he posted a full rundown of what he did. I highly recommend that article, which is both informative and a delightful, entertaining read.
As Alex points out:
“People post their boarding passes all the time, because it’s not clear that they’re meant to be secret”

Your or Your Child’s Citizenship or Residency Papers
As an Australian ex-pat based in the US, I get the pride in gainling permanent residency or aquiring local citizenship. Yet the frequency with which people publicly share documents with information that could be used for identity theft on Instagram and Reddit, closed but large Facebook groups (such as Australians in America), or with their many hundreds or thousands of Facebook friends, always astounds me.
If you are going to post a picture with high enough resolution to read one of these documents, remember to censor all fields that you sometimes get asked to verify your identity, including innocuous ones that anyone who personally knows you may deduce, like place of birth, full legal name, birthday, etc.
Most photos of identifying documents in a wide or medium shot photograph, such as an adult holding up a piece of paper are too low resolution to read the document. The common thing I see is people posting photos of their baby next to a full size (not passport or ID card sized) citizenship document. By all means post a photo of your baby with a cute onsie and perhaps a prop representing your country’s culture, but do remember to redact the document.
Posting A Photo or Footage of a Key
Keys for consumer-grade locks are easily reproducible, from even a photo. In fact, it’s probably a good idea to keep a photo of any important keys in a safe place, in case you ever need to reproduce them when in a bind.
Duplicating a key from a photo is easy, as explained in the below video.
A big no-no is posting a photo of a key online, which I have seen more than once used to demonstrate an item’s size in an online for-sale listing. “Key for scale” may as well be enclosing a copy of your key for anyone to access your home. I have contacted several people over the years advising them to switch out their photo.
An extreme example of this involved a 2006 television broadcast of a set of prison keys in London, resulting in the production company being sued for £300,000. As one Reddit commenter pointed out, the large cost stems not from the cost of new keys and changing locks, but from the time involved in taking each prisoner out of their cell under guard for 30 minutes each.
Your Crypto Private Key
Similar to the above key incident, in 2013 during a “12 days of Bitcoin”, Bloomberg TV showed a private Bitcoin gift certificate QR code key in glorious high definition for 10 seconds straight, prompting one reddit user to prompty post about it on Reddit. Within minutes the $20 worth of bitcoin was stolen, and the thief posted proof. In 2022, that $20 worth of bitcoin would be worth a four figure number.

Your Password Reset Email
Sadly I have no screenshot or link to share for this one but it’s pretty simple. Years ago someone arrogantly posted on Reddit claiming that their IT security was great, despite people trying to hack into their accounts. Someone tried to reset their Reddit password, and they posted a screenshot of the email. Well, all someone needed to reset the password was to type in that long link, which they promptly did. The hacker used the account to post what they did.
The hacker then contacted the person to give them the new password, but they learned their lesson.
Your Winning Gambling Tickets
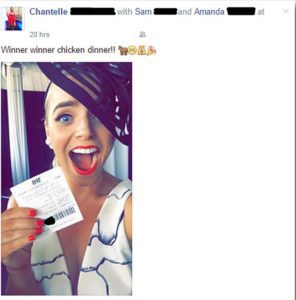
In 2015, travel agent Sam Smith, 27, and his friend Chantelle posted photos of their 100-to-1, $825AUD winning horse race bets to their respective social media profiles. Someone used the barcodes to cash in their winnings on an automated machine. Both profiles’ security settings only allowed the posts to be seen by friends, meaning it was stolen by someone each knew…or at least on their vast friends lists. (Another reason to only accept friend requests from people you actually know.)
The thief was captured on CCTV but no word on whether they were caught.

That’s what you get for counting your horses before they hatch.
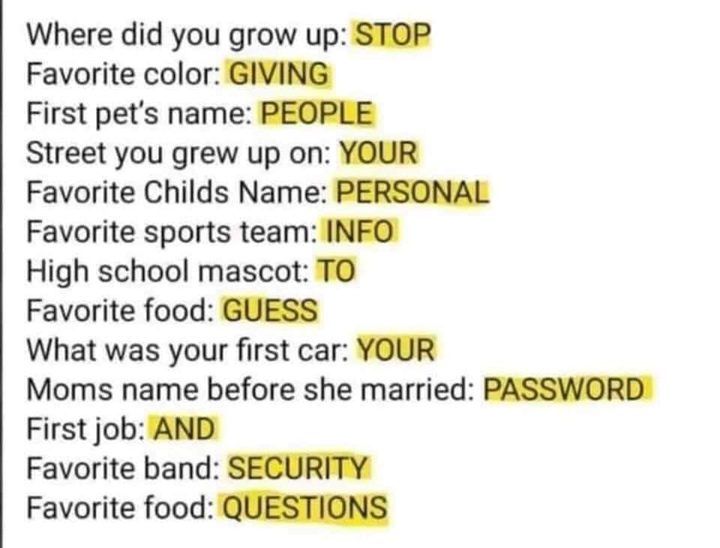
Stupid Viral Questions
The common “secret question and answer” method of password recovery and the now-thankfully-dead method of password-hints were already deeply flawed long before there were viral memes asking you to publicly answer silly, fun questions. As the now-viral Facebook post by Alan Belniak points out, though nostalgic, and a way to engage with others, they’re actually handing out the keys to your accounts passwords. No matter how benign these seem, there’s always a chance an account you created years ago is protected by the answers you give.
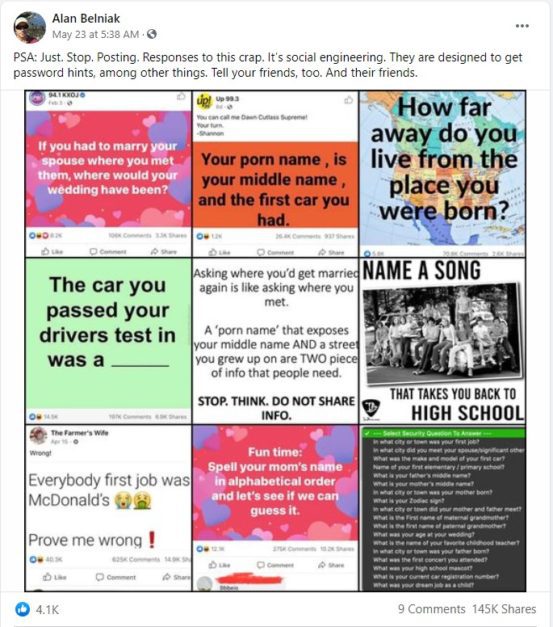
This is called “Social Engineering” which CSO (Chief Security Officer) Magazine defines as
“the art of exploiting human psychology, rather than technical hacking techniques, to gain access to buildings, systems or data”.
Or to put it another way…
Location Identification Via Reflection…In Your Eyes
Scrubbing location data from your photo metadata might not be enough. In this truly horrific example that puts CSI to shame, 21-year-old Japanese idol Matsuoka Shinan was attacked after a stalker identified her location from a photo. Not based on background information, or a convenient polished surface, but rather based on location clues he gathered from the reflections in her eyes in a selfie she posted at her local train station. He used Google Maps Streetview to determine the location, confirmed in person, then laid in wait for before he followed her home and attacked her.

Will red-eye reduction algorithms make a comeback to scrub or obscure reflections in our eyes? Probably not, as this was a truly extreme case involving a stalker, but it does make you wonder what’s next.
Your Hands or Fingernails
In addition to unique fingerprints, morphological features in the backs of our hands and fingernails can be used to uniquely identify us. Jus like fingerprints, vein patterns in our hands are one-offs, developed in the womb by cells that assemble spontaneously, rather than following a pre-established blueprint. Unlike fingerprints and palm prints, veins have the advantage of being enclosed by skin and can’t be altered. This alone is unique and unfalsifiable enough to be used as the basis for the Amazon One palm payment system.
Coupled with scars, freckles, birthmarks, moles, nails and skin creases we accumulate, hands are also unique enough to be used by forensics teams to identify and convict multiple paedophiles based on photographic evidence. One matched piece of evidence was “an unusually shaped lunule, the white area at the base of the nail.”
Interestingly, in addition to age trends, the data has some gender trends. According to this Wired article
“men have 50 per cent more scars than women, but right-handed men are more likely to scar their left hands, while right-handed women tend to scar their right – no one knows why.”
Presumably, people who work with their hands are more likely to have more scars than those who do not.
Hand matching is still in its early stages, but photographic evidence preserves well. Who knows how many cold cases could be solved this way, or where the science and technology will go. For now, Amazon claim “you’ll need to intentionally scan your palm for it to work”, but who knows where corporations, governments, or individuals could take this.
Is Online Anonymity Even Possible?
So you’ve watched your corporate training videos on security, you use a password manager, and practice good common sense about what you post. Those of us not being targeted by a government, law enforcement, an identity thief, or a stalker are probably fine. We live in an era where it’s not uncommon to freeze one’s credit, get a PO box, and for some, use a private browser like Brave or TOR. Digital security is like home security in that no home is impenetrable to a dedicated burglar or the government, and the best we can hope for is to deter crimes of opportunity and make things very, very hard for even a dedicated nefarious agent. Despite the liklihood that one day a simple wave or middle finger gesture may not be as anonymous I’d like, I sleep well at night.
For now my dreams are private, although now I think about it I should probably check the privacy policy for my sleep monitoring app…
Protect Your Security With Further Reading:
- Anything written by or said by former hacker Kevin Mitnick
- Never Post A Picture Of Your Boarding Pass On Social Media | secjuice
- Why You Should Never Post Pictures of Your Flight Tickets or Keys | Vice